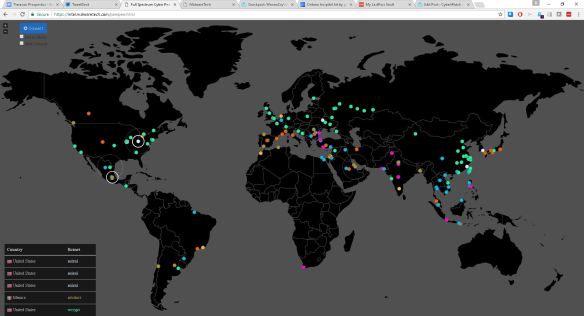
real time botnet tracking map by http://www.malwaretech.com
The number of countries impacted is over 1 00. We are expecting version 2.0 to hit by Monday, because that’s the nature of these attacks: the attackers know when they have their victims over a barrel, and the maximize the opportunity. Microsoft has issued patches. But what everyone can and must do, over and above applying these specific patches, is this:
- Ensure you have full, and working backups that are offline and removed from the network.
- Have a Disaster Recovery/Business Continuity plan that specifically addresses cyber events like this one
- Be ready with a crisis communications designated spokesperson and prepared statements. If you’ve been hit, and things are going terribly wrong, then you don’t want to be dealing with that and trying to say the right things to press, staff, stakeholders
- Check in with and listen to your network and sysadmins. They know what’s going on out there. They’ve seen the sh*t that happens, what breaks, and why
- Don’t evade or deflect this topic. Don’t underplay it, and of course don’t focus on the fear. Have honest discussions with your staff because this is how you creating lasting awareness and create change in behaviours that will better secure your organization
I follow these two experts on the risks to specialized systems, notably ICS or Industrial Control Systems and SCADA, Supervisory Control and Data Acquisition. Note that medical facilities, mass transit, manufacturing and utilities all rely on these specialized systems that are proprietary; are often set up with hard coded or default passwords that are NOT secure; and with older equipment that just can’t be upgraded so is left to run unpatched until it fails. There is so much more we need to address.
Here is a global snapshot (per CTV news):
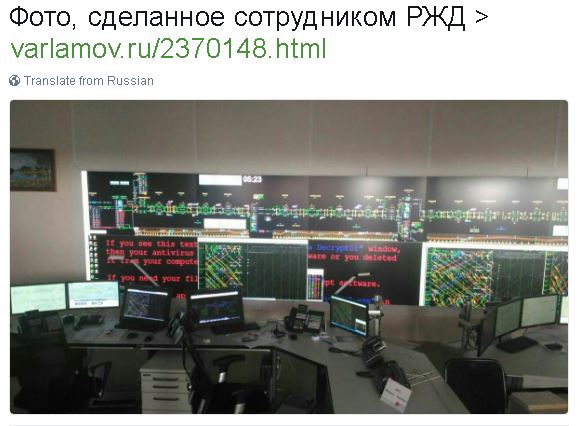
Russian Train Control Center Ransomwared
EUROPEAN UNION: Europol’s European Cybercrime Centre, known as EC3, said the attack “is at an unprecedented level and will require a complex international investigation to identify the culprits.”
BRITAIN: Britain’s home secretary said the “ransomware” attack hit one in five of 248 National Health Service groups, forcing hospitals to cancel or delay treatments for thousands of patients — even some with serious aliments like cancer.
GERMANY: The national railway said Saturday departure and arrival display screens at its train stations were affected, but there was no impact on actual train services. Deutsche Bahn said it deployed extra staff to help customers.
RUSSIA: Two security firms — Kaspersky Lab and Avast — said Russia was hit hardest by the attack. The Russian Interior Ministry, which runs the country’s police, confirmed it was among those that fell victim to the “ransomware,” which typically flashes a message demanding payment to release the user’s data. Spokeswoman Irina Volk was quoted by the Interfax news agency Saturday as saying the problem had been “localized” and that no information was compromised. Russia’s health ministry said its attacks were “effectively repelled.”
UNITED STATES: In the U.S., FedEx Corp. reported that its Windows computers were “experiencing interference” from malware, but wouldn’t say if it had been hit by ransomware. Other impacts in the U.S. were not readily apparent.
TURKEY: The head of Turkey’s Information and Communication Technologies Authority or BTK says the nation was among those affected by the ransomware attack. Omer Fatih Sayan said the country’s cyber security centre is continuing operations against the malicious software.
FRANCE: French carmaker Renault’s assembly plant in Slovenia halted production after it was targeted. Radio Slovenia said Saturday the Revoz factory in the southeastern town of Novo Mesto stopped working Friday evening to stop the malware from spreading.
BRAZIL: The South American nation’s social security system had to disconnect its computers and cancel public access. The state-owned oil company Petrobras and Brazil’s Foreign Ministry also disconnected computers as a precautionary measure, and court systems went down, too.
SPAIN: The attack hit Spain’s Telefonica, a global broadband and telecommunications company.



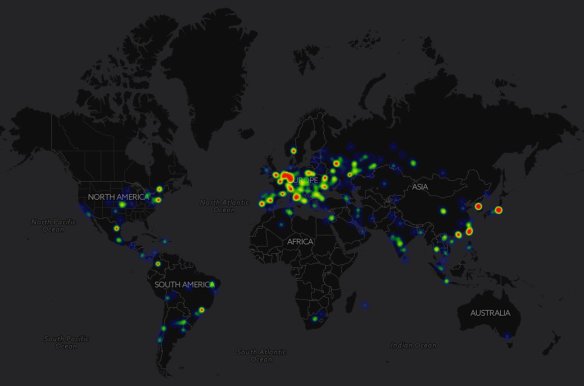
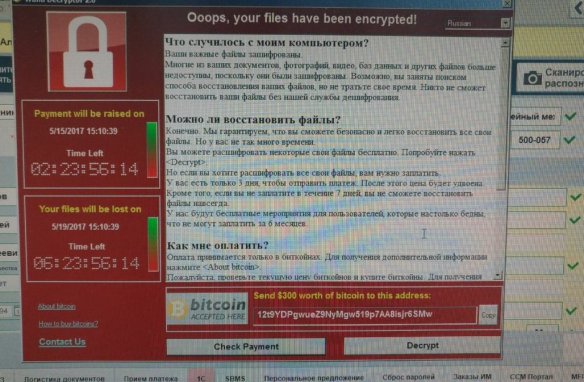




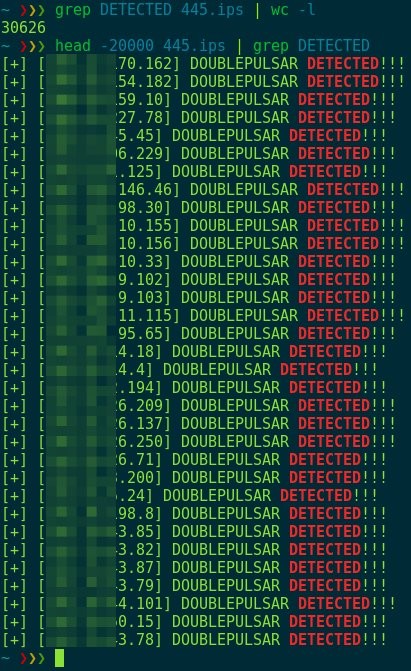
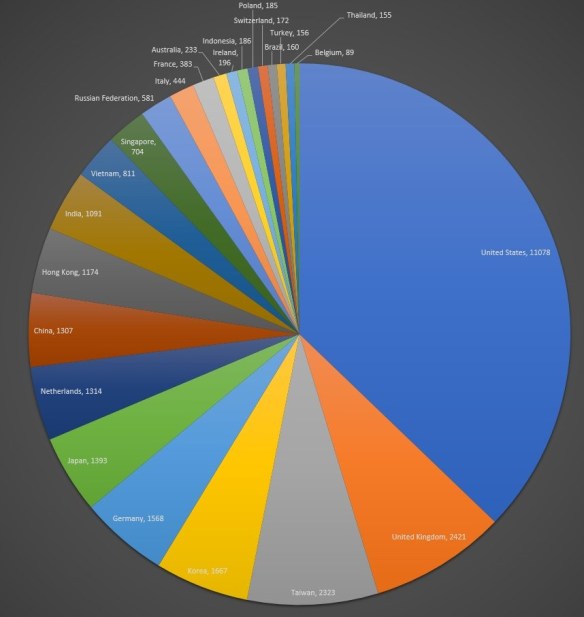


 In the realm of cyber criminals, The Lazarus Group are somewhat nebulous, hard to pin down, and known for their ability to die off and then resurrect themselves, hence their name. They’ve been identified as operating out of North Korea. To me, that means North Korea gives them a safe haven in return for services rendered. They are the bag man for their host supplying “dirty deeds”, just not done dirt cheap. Because nation states don’t do this stuff for themselves when they need to remain one step removed. Let me state that things are no where near this simplistic, and yes, China factors into this as well. But no surprise there given the long-standing partnership between China and North Korea.
In the realm of cyber criminals, The Lazarus Group are somewhat nebulous, hard to pin down, and known for their ability to die off and then resurrect themselves, hence their name. They’ve been identified as operating out of North Korea. To me, that means North Korea gives them a safe haven in return for services rendered. They are the bag man for their host supplying “dirty deeds”, just not done dirt cheap. Because nation states don’t do this stuff for themselves when they need to remain one step removed. Let me state that things are no where near this simplistic, and yes, China factors into this as well. But no surprise there given the long-standing partnership between China and North Korea.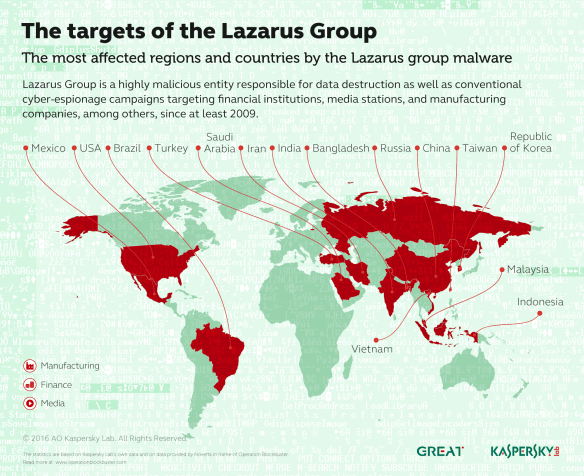 Where does this lead? Well, I did allude to the possibility of global economic chaos being used in the games nations play, because it’s all about the power and money is just a means to that end. Now we have news reports saying how nation states have resorted to robbing banks, and what a terrifying prospect that is. According to Richard Ledgett, Deputy Director of the NSA, in a story by the
Where does this lead? Well, I did allude to the possibility of global economic chaos being used in the games nations play, because it’s all about the power and money is just a means to that end. Now we have news reports saying how nation states have resorted to robbing banks, and what a terrifying prospect that is. According to Richard Ledgett, Deputy Director of the NSA, in a story by the 