 Welcome to the grey zone where politics and cyber meet. APTs or advanced persistent threats, are one of my favourite acronyms (but then you know how I am intrigued by Stuxnet and cartels), and essentially are how nation states get their digital digs at each other. Usually the intention is to get information, because knowledge is power. Cyberespionage can give a competing nation a real competitive advantage in the world economy, among other things. But sometimes, there is a need to control more, and that is where weaponizing code takes on a whole new nasty.
Welcome to the grey zone where politics and cyber meet. APTs or advanced persistent threats, are one of my favourite acronyms (but then you know how I am intrigued by Stuxnet and cartels), and essentially are how nation states get their digital digs at each other. Usually the intention is to get information, because knowledge is power. Cyberespionage can give a competing nation a real competitive advantage in the world economy, among other things. But sometimes, there is a need to control more, and that is where weaponizing code takes on a whole new nasty.
The keyword here is “persistence.” First, attackers must find their way into the networks of the target. Usually, they employ targeted spear phishing, painstakingly staking out the right victim to receive that loaded email. The investment of time and money at this point is essential, so as not to tip anyone off. And the emails are crafted so carefully, picking up on points tailored to that recipient so that they will open it, and launch the attachment that will create an entry point for the attacker. There is a reason why phishing is at the heart of so many breaches.
Now, imagine a video game, where you must progressively meet the challenges of each level to go higher. That is the attacker moving through the network, acquiring credentials to gain access to the crown jewels. The strategy is to find someone lower level, then work your way up. Hence, persistence, because this is an investment of both time and patience. Expect the key executives or decision makers to be well-guarded, with access and authorization controls in place. Not the case for someone lower on the food chain. All an attacker needs is to gain access. As proven repeatedly, once in, they can take all the time they need to find what they want. Case in point: the attack on the Ukraine power grid in December 2016. The attackers were in that system for over nine months, collecting what they needed, notably credentials for the Virtual Private Network, that enabled them to jump the security gap onto the restricted side. As Stuxnet taught us, there is no such thing as air-gapped security.

We know the Russians hacked the US; we know China hacked the US and Canada; and yes, the US has hacked someone too. These are the games nations play. The trick, of course, is not to get caught before you have the prize. And when you do get caught? Well, as we’ve seen play out, nothing really bad happens. Just expect that your victim will be in your systems. Unless information isn’t the endgame and control is. Then, be prepared for something to go bump in the night.
Shamoon is devastating wiper malware that took out a massive swath of Saudi Aramco when it first debuted in 2012. Linked to Iran, and an ongoing feud in the region between key players, it was a targeted attack against the oil giant, damaging or destroying 35,000 computers. Sec Def at the time, Leon Panetta, described it as “probably the most destructive cyber attack on a business.”
Wiper malware was used against business targets in December 2014 destroying the systems in a Vegas casino, The Sands, after owner Sheldon Adelson advocated using nuclear weapons against Iran. The US “publicly cited Iran as the culprit”. Then Disstrack was used again in December 2015, in the attack that brought Sony to its knees. These aren’t gangs using cybercrime for monetary gain. These are the equivalent of acts of war, given the level of damage done.
Fast forward to late 2016. Two major attacks happened in Saudi: November 17 taking out systems at the airport and other Saudi government agencies, and then again on November 29. Then, on January 23 there was another attack. The malware used was almost identical to the original Shamoon, aka Disstrack. Except there were a few key enhancements. According to Andrew Plato, CEO of Anitian Enterprise Security
“What is really worrisome about this is it’s just outright destructive. It isn’t really trying to steal anything. It’s the closest things we’re going to get to a cyber bomb”.
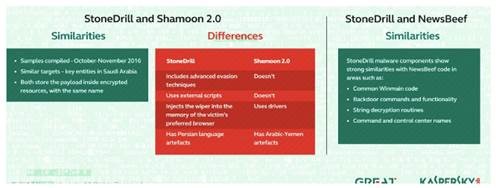
The new version, dubbed Shamoon 2, spread through the local network using legitimate counts belonging to users and administrators, with complex passwords likely obtained from an earlier attack. Remember what I said about persistence? This new version, however went on to attack VDIs, or Virtual Desktops, which previously could have offered some protection because of their ability to load snapshots of systems that were wiped. Now Shamoon had migrated from just Windows-based systems to Linux in the attacks on VDIs.

Now, I don’t want to be alarmist and spread FUD everywhere. Yes, this is serious and destructive. Like Stuxnet, it broke things. And that’s the differentiator. So far, the line hasn’t been crossed where breaking things was deliberately done to harm people. Because as Archer would say: You want cyberwar? Because that’s how you get cyberwar.
While the expectation is that Iran is once again behind the attacks, Symantec has revealed there are multiple parties involved. More than one entity, so collaboration and cooperation. The report is that an entity known as Greenbug may have assisted in getting the credentials needed for access. Palo Alto reported on a campaign known as Magic Hound which targeted energy, technology and government with ties or locations in Saudi. There were links between Magic Hound and two other actors with Iranian ties: Charming Kitten and Rocket Kitten. Finally, putting all this together was the group Timberworm or Cobalt Gypsy. Per Symantec, Timberworm was behind the January 23 attacks.
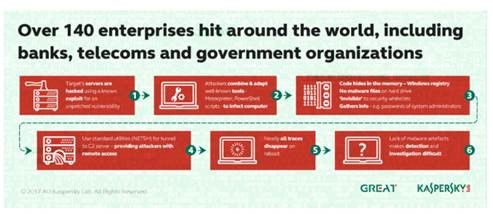
Here’s the play by play. First, Timberworm used spear phishing emails with weaponized documents (we warned you about those Office Macros!) to gain initial access into the network. Once there, they used custom malware, along with leveraging existing sysadmin tools to avoid detection, and help them achieve persistent remote access. Quick FYI: custom malware is a hallmark of major organized cybercrime groups or nation state attacks because it costs a lot of time and money to craft, and the stakes are going to be very high.
Apparently Greenbug and Timberworm have been active, penetrating organizations beyond Saudi. Note that Shamoon, however, was only used against the Saudi target. Timberworm is a large operation, as is Greenbug, with targets in a range of areas. We know who they are now, what they can do, and that they have a shared interest. What we don’t know: the endgame. I’m waiting for that other shoe to drop.
http://www.zerohedge.com/news/2016-12-01/another-false-flag-destructive-iranian-hackers-allegedly-wreak-havoc-saudi-computer-
http://www.securityweek.com/shamoon-2-variant-targets-virtualization-products
http://www.securityweek.com/multiple-groups-cooperated-shamoon-attacks-Symantec
http://www.archersecuritygroup.com/second-wave-bomb-malware-hits-saudi-arabia/
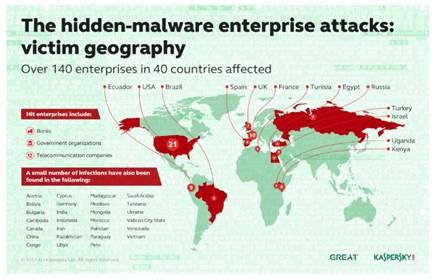
 Attacks were predominantly in Europe, the staging ground for Russian cybercriminals before they launch their malware on America. Attacks are now heavy in the Netherlands, and have landed on American shores as confirmed by Microsoft’s Malware Protection Center.
Attacks were predominantly in Europe, the staging ground for Russian cybercriminals before they launch their malware on America. Attacks are now heavy in the Netherlands, and have landed on American shores as confirmed by Microsoft’s Malware Protection Center.
 Welcome to the grey zone where politics and cyber meet. APTs or advanced persistent threats, are one of my favourite acronyms (but then you know how I am intrigued by Stuxnet and cartels), and essentially are how nation states get their digital digs at each other. Usually the intention is to get information, because knowledge is power. Cyberespionage can give a competing nation a real competitive advantage in the world economy, among other things. But sometimes, there is a need to control more, and that is where weaponizing code takes on a whole new nasty.
Welcome to the grey zone where politics and cyber meet. APTs or advanced persistent threats, are one of my favourite acronyms (but then you know how I am intrigued by Stuxnet and cartels), and essentially are how nation states get their digital digs at each other. Usually the intention is to get information, because knowledge is power. Cyberespionage can give a competing nation a real competitive advantage in the world economy, among other things. But sometimes, there is a need to control more, and that is where weaponizing code takes on a whole new nasty.

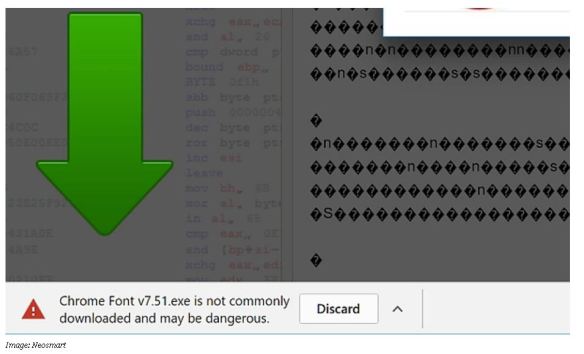 But, if you play it safe and do as Google says, click Discard and don’t download. You’ll avoid ransomware.
But, if you play it safe and do as Google says, click Discard and don’t download. You’ll avoid ransomware.