PLCs with hard-coded key vulnerabilities is a 10 out of 10 severity per Ars Technica
PLCs are programmable logic controllers used in within industrial control system or ICS: manufacturing, industrial plants, power plants. Be concerned. Be very concerned. While they look like the desktops and keyboards we used to use at the office, this is specialized equipment that helps run our daily lives, keeps our lights on, keeps us safe. Referred to as Critical Infrastructure, it’s the ideal target for nation-state attacks where revenge and control collide.
When malware and tactics are weaponized for destruction, bad things happen like:
- power plant sabotage by Black Energy malware in the Ukraine
- cyber attacks water treatment plants by Iran in Israel
- industrial safety system malfunctioning by Triton malware
- centrifuges spin out of control in a nuclear facility with Stuxnet.
On Feb 26, US CISA issued a warning here for CVE-2021-22681, involving the extraction of a secret encryption key hard-coded in Logix brand PLCs from Rockwell Automation. Key point here (sorry had to) is don’t hardcode or embed passwords and security keys as a fundamental good security practice. This makes the PLCs vulnerable to attack by someone remote and with low skill levels, who could then alter their configuration or their application coding. Do you want bad things? Because this is how you get bad things. How bad?
“Any affected Rockwell Logix controller that is exposed on the Internet is potentially vulnerable and exploitable”
Sharon Brizinov, principal vulnerability researcher at Claroty
Which brings me to my second “key” point: don’t expose sh@t you value online. Because people know how to go hunting with Shodan, and omg they things they find!
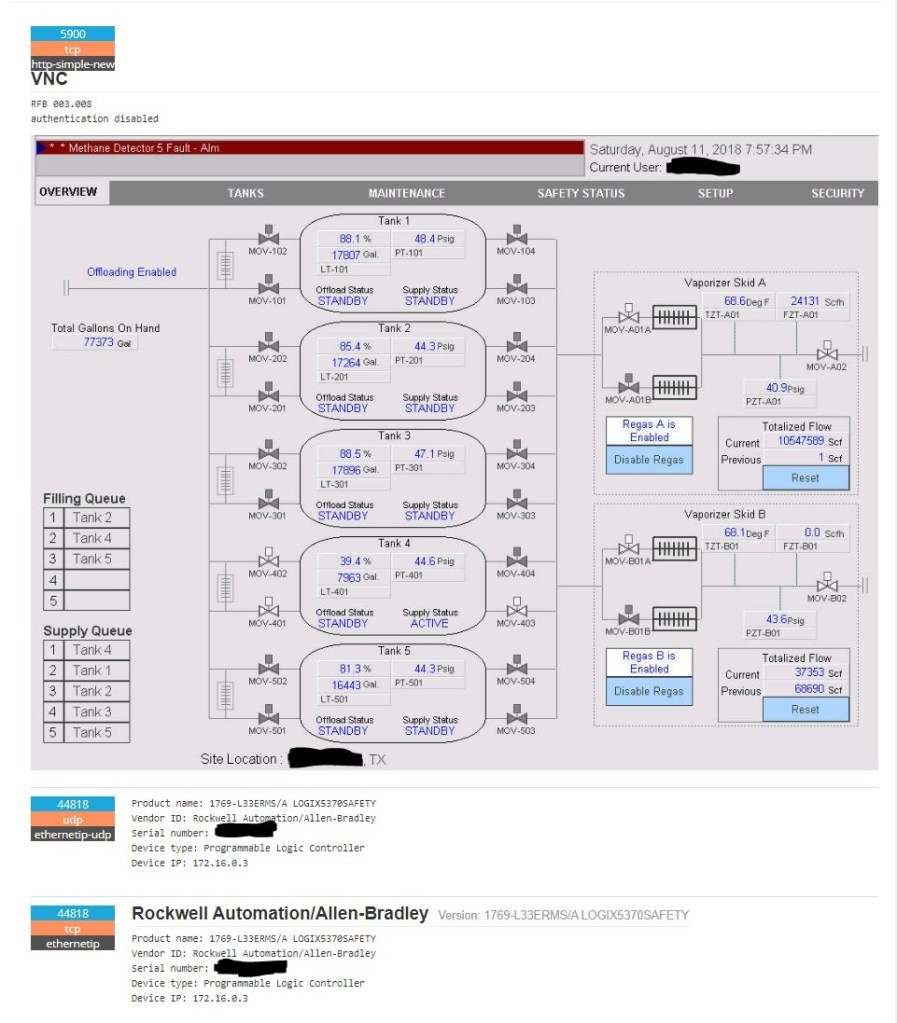
There’s another thing that troubles me. Maybe I’m being petty but apparently Claroty told Rockwell “Hi! You may have a security problem” back in 2019. I know we lost a whole year with 2020 but still, it took til last Thursday for anything to be said.
Pretty much any Rockwell Logix PLC is at risk. It’s a long list. How about a patch for that? Well, not just yet. But there is an advisory now available from Rockwell with mitigations and instructions. You can read the write up by Claroty here and you probably should.
Want to know more? In addition to this excellent article by Dan Goodin forArs Technica, I can recommend reading “Sandworm” by Andy Greenberg and “Countdown to Zero Day“ by Kim Zetter. Here is where I get to cheer on the work being done by the team of dedicated security researchers who specialize in the field of ICS and SCADA at Dragos Inc., Bryson Bort and the awareness he’s bringing, and my friend Chris Sistrunk at Mandiant who helps keep the power grid safe and our lights on among many other things.









