Security breaches, mass DDoS attacks, ransomware mutations. No question about it – the challenges to information security are constant and ever-changing. Over the past twelve months, InfoSec has had to deal with threats not only of a greater magnitude in complexity but also in sheer volume. So in our concerted, and at times hasty, efforts to keep up with all that’s out there, are we leaving ourselves exposed? Do we need to double-back and cover our tracks?
Fact is, there is a lot to keep up with, even for security super-heroes. Given the nature of the beast, we’re always looking forward, trying to keep up or gain a little ground to ready ourselves for the next challenge. But what about those “backdoors” we just closed?
 Cleaning up after mass events like ShellShock/Bashbug and Heartbleed isn’t straightforward. Sadly, one patch does not fit all when there are multiple iterations of operating systems and devices. And the truth is – there just aren’t enough good people or hours in a day to comb through all the stuff out there to find and fix what’s at risk, much as we want to. Much as we need to. What happens next is inevitable. The adversary takes advantage, finds the hole, and builds exploits that we then must find and shut down in a series of blocks and tackles.
Cleaning up after mass events like ShellShock/Bashbug and Heartbleed isn’t straightforward. Sadly, one patch does not fit all when there are multiple iterations of operating systems and devices. And the truth is – there just aren’t enough good people or hours in a day to comb through all the stuff out there to find and fix what’s at risk, much as we want to. Much as we need to. What happens next is inevitable. The adversary takes advantage, finds the hole, and builds exploits that we then must find and shut down in a series of blocks and tackles.
Here’s a recent case in point: Shellshock and QNAP. Shellshock doesn’t just impact servers. It impacts devices connecting to these servers through the internet: wireless access points, routers, smart fridges, video cams, webcams, even light bulbs. You can patch a server. It’s not so easy to patch a fridge. The real challenge has been to identify and patch all those different exposed devices. QNAP makes network attached storage devices that are popular world-wide. And therefore ideal targets for Shellshock exploits.
While QNAP did issue a firmware patch in October, Shellshock worm exploits were detailed later in December. The worm targeted a particular CGI script, /cgi-bin/authLogin.cgi, which could then be accessed without authentication. That would allow attackers to launch a shell script that could in future download more malware. Essentially, keeping the backdoor open.
One of the interesting things noted about this worm, per Kaspersky’s detailed write up, was that the script it made then downloaded and installed QNAP’s Shellshock patch. Yes! But in a move that was strictly territorial to keep other opportunistic attackers out.
Kaspersky advised that
“IT staff responsible for these devices security should apply patches themselves, or a worm will do it. At a price”
I’ve followed up with QNAP, and nothing else has been issued. The onus is on the users to identify and patch their products. Need I say more?
It’s easy to lose track when the tyranny of the urgent sets our agendas for us. And it’s hard to be proactive when you’re busy fighting fires. But the fact is we need to keep watching those backdoors – because they don’t always shut completely.
This post was featured on DarkMatters, the security blog by Norse Corp
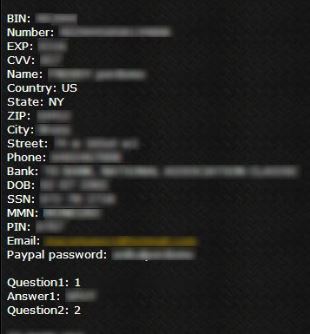
The lead illustration is an actual screencapture of Shellshock malware by MalwareMustDie.org, a whitehat security research workgroup