They came for the money, they stayed for the data. There is far more at stake in financial services than dollars and sense. The past twelve months have shown how far attackers are willing and able to go; banks are known for their conservative pace in adopting new strategies, and attackers are literally banking on it.
As the saying goes, “In God we trust”. In banks, maybe not so much. According to a recent report by Capgemini, one in five bank execs are “highly confident” in their ability to detect a breach, never mind defend themselves against it. Yet “83% of consumers believe their banks are secure from cyber attack”. One in four banks report they’ve been attacked, but only 3% of consumers believe their bank has suffered a breach. Never mind the money. How about the data? Survey shows that 71% of banks don’t have a solid security strategy in place, nor do they have adequate data privacy practices. The numbers are not good. Only 40% of banking and insurance companies have automated security intelligence capabilities for proactive threat detection
After following the trail on the SWIFT bank heists last year, I’ve paid close attention to banking malware, threat actors, and points of failure. What worries me is what’s coming as digital payments become the norm, and digital identities take hold in developing nations who lack the infrastructure or regulation to secure or enforce. Given what we already know, what does this recent history of attacks tell us?
Polish Banks
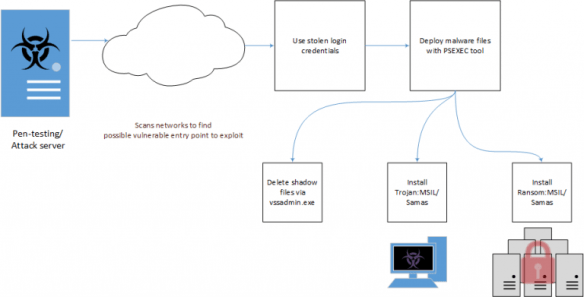
The recent series of targeted malware attacks against Polish banks was identified in January this year, but attackers went after the data, not money. After noticing unusual network activity, like traffic to “exotic” locations and encrypted executables that nobody knew of, and unauthorised files on key machines in the network, several commercial banks confirmed malware infections. Investigations revealed infection stemmed from a tampered JS file from the webserver of the Polish financial sector regulatory body. This was actually part of a wider campaign that has gone after financial institutions in over 30 countries. According to researchers from both BAE Systems and Symantec, the malware used in Poland can be linked to similar attacks around the globe, and there are marked similarities to tools used by the cybercrime group Lazarus, although no confirmation has been made. Targets were led to compromised sites of interest to them, watering holes, which were malicious sites that injected code and directed the targets to a customized exploit kit. This kit contained exploits against known vulnerabilities in Flash Player and Silverlight. What’s interesting is that the exploits were only activated for certain visitors: those with IP addresses from specific ranges. Per Symantec, “The IP addresses belong to 104 different organizations located in 31 different countries … The vast majority of these organizations are banks, with a small number of telecoms and internet firms on the list.” 15 of these are from the US. The infection downloaded enables recon on the compromised system. Again, this tool is similar to those used in past by the Lazarus group. Now every major security group has published their opinions and analysis on what was originally all but overlooked as some malware that spread from the regulatory body’s server.
Fileless Malware Attacks
In January of this year, there were reports around the globe of attacks on banks using fileless malware. The malware resided solely in the memory of compromised systems. This is not signature based malware that can be referenced and detected. According to Kaspersky, 140 enterprises in 40 countries have been hit. And forensics cannot help us:
“ memory forensics is becoming critical to the analysis of malware and its functions. In these particular incidents, the attackers used every conceivable anti-forensic technique; demonstrating how no malware files are needed for the successful exfiltration of data from a network, and how the use of legitimate and open source utilities makes attribution almost impossible.”
But the infections are hard to identify so that number could well be more. Further complicating things is the use of legitimate and widely used sysadmin and security tools like PowerShell, Metasploit and Mimikatz for malware injection. In a range of incidents, the common denominator seems to be embedding PowerShell in the registry to download Meterpreter. From there, the attack is carried out using the native Windows utilities and sysadmin tools. Per Kaspersky:
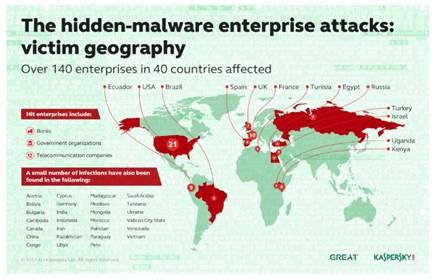
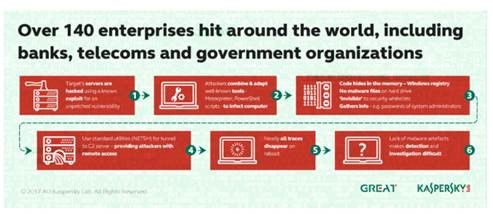
The new fileless malware hitting banks is Duqu 2.0, which Kaspersky found on it corporate network in 2014, but only after it went undetected for 6 months because it lives almost completely in the memory of the computers. Duqu 2.0 is derived from Stuxnet. The malware renames itself when an infected computer is rebooted so digital forensics has a tough time finding traces. The calling card seems to be the unusual embedding of PowerShell into the registry to download Meterpreter. Duqu 2.0 is derived from Stuxnet. Reports aren’t saying how the malware spreads.
TESCO Bank Attack
In November 2016, Tesco Bank, a British retail bank chain with 7 million customers, warned its customers to watch for suspicious money withdrawals. Unfortunately, when customers who noticed money was missing from their accounts reached out to the bank, many could not get through. Approximately 20,000 accounts were hit. Tesco briefly halted online transactions in response. The attack seemed to stem from a “systemic failure of security around Tesco’s core database”. Recommendations include having controls in place to alert on changes to key files and configurations. As well, file monitoring integrity and Configuration Management Security ensure that if and when changes are made, they are valid and validated.
Take the Money and Run: COBALT, ATMs and ‘Jackpotting’
There was a distinct rise in ATM attacks over 2016. The latest siege, Cobalt, covers a wide swath across the UK, Spain, Russia, Romania, the Netherlands, much of Eastern Europe and Malaysia. According to Group IB researchers, a large number of machines are attacked at once, and Cobalt appears to be linked to cybercrime syndicate Buhtrap. The malware used causes infected machines to spit out cash in an attacks known as “jackpotting”. Noteworthy is how this is being described as “the new model of organized crime”. The FBI issued warnings to US banks following those ATM heists, taking into account the attacks in Taiwan and Thailand, when thieves grabbed over 260,000 pounds from Thailand’s Government savings bank and $2.5 million from Taiwan. The world’s two largest ATM manufacturers, NCR and Diebold Nixdorf, worked to manage the threat.
Lloyd’s Bank Hit by DDoS Attack
In January the venerable Lloyd’s Bank of London was struck by a DDoS attack that lasted two days. Attackers tried to crash the Lloyd’s site, causing issues for customers and impacting some access to online banking. The bank did not lose money, nor data, nor was the impact significant. Law enforcement is investigating.
Attacks on Banks in the SWIFT System
Banks rely on messenger systems to conduct transfers back and forth. In 2016, a series of targeted attacks on banks in the trusted SWIFT messenger system came to light after a massive heist on the Bank of Bangladesh. Apparently the attacks are evolving, and SWIFT has told member bank, in an undisclosed letter from Nov. 2, that “attacks on its systems have only become more sophisticated in their strategies”. “The threat is very persistent, adaptive and sophisticated – and it is here to stay”. This is despite the work by regulators globally to toughen bank security measures. And the word is that “a fifth of them are hitting paydirt for the attackers”, per Stephen Gilderdale, head of SWIFT’s Customer Security Programme. Now the hackers exploit tech support software to gain access. Then send victims phony payment instructions via SWIFT network. SWIFT emphasizes that all those attacks detected “exploited SWIFT interfaces used by its customers” but that the SWIFT communications network itself was not impacted. In light of this, warnings are being issued to small businesses to realize the threat to them is real. Scams have become more sophisticated and will continue to evolve.
Sources:
https://badcyber.com/several-polish-banks-hacked-information-stolen-by-unknown-attackers/
https://securelist.com/blog/research/77403/fileless-attacks-against-enterprise-networks/
https://www.symantec.com/connect/blogs/attackers-target-dozens-global-banks-new-malware-0
https://baesystemsai.blogspot.sk/2017/02/lazarus-watering-hole-attacks.html https://threatpost.com/fileless-memory-based-malware-plagues-140-banks-enterprises/123652/
http://www.welivesecurity.com/2017/02/16/demystifying-targeted-malware-used-polish-banks/?utm_source=organic%20twitter&utm_medium=news&utm_campaign=WLS http://economictimes.indiatimes.com/industry/banking/finance/banking/indian-banks-are-waking-up-to-a-new-kind-of-cyber-attack/articleshow/56575808.cms
https://www.f-secure.com/documents/996508/1030743/cyber-security-report-2017