Photo by Tristan Schmurr, Cyberscoop Apr 21
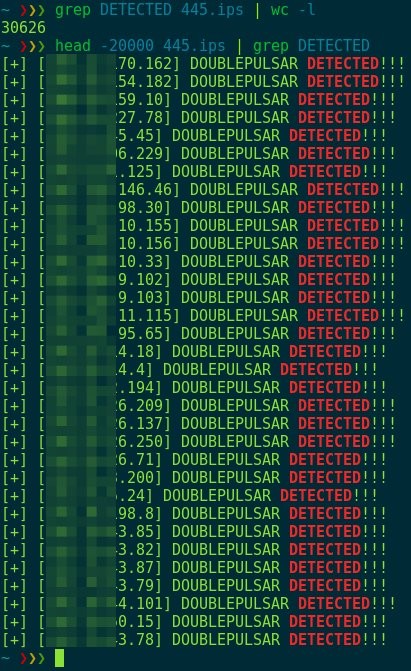
A good friend of mine, with the handle @loneferret, shed some clarity on the massive dump of exploits two weeks back by the ShadowBrokers. I haven’t said my piece here but believe me I shared my thoughts online as things developed. And Double Pulsar, a backdoor implant, is just that gift that keeps on giving as countless systems appear to be infected. John Matherly of Shodan cited finding at least 45k as of April 21. Dan Gentler aka @viss describes it perfectly as “a loading dock for extra malware”. There is much to be said, but I quite liked the way my friend spun things, so without further ado …
Yet another MS17-010 blog post.
However, the more noise that is generated, the more people will update their systems.
About a week ago now, a bunch of exploits were leaked by a group calling themselves “Shadow Brokers”, or “ShadowBrokers”; both spellings are used it seems ¯\_(ツ)_/¯.
These exploits are serious stuff, as they affect almost every version of Windows, both professional and home (what you have at home most likely), as well as, server editions. There are Linux exploits as well but that’s for another post …
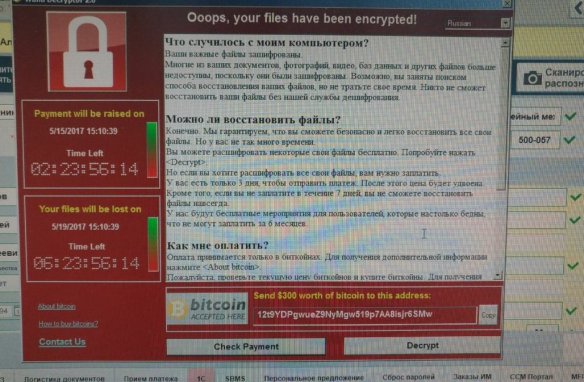
Barely a week has passed, and reports of ransomware being delivered using “Eternalblue” are popping up. Reports of systems being compromised by what we can only assume are “script-kiddies” have also surfaced.
Why keep reading? My goal here isn’t to give a technical lesson nor a course in exploitation, but to spread awareness. When these types of vulnerabilities & exploits are made public, havoc isn’t too far behind.
As a pen-tester the news of exploits originating from an NSA dump was exciting. It gives some insight on what sort of tools\exploits the notorious agency has, and ensures some level of job security for me (I know selfish). But what does this mean for the corporate user? What does this mean for the average user? In a nutshell if you haven’t installed the most recent security updates, you risk having your data stolen, deleted, or your hard drive encrypted and held for ransom.
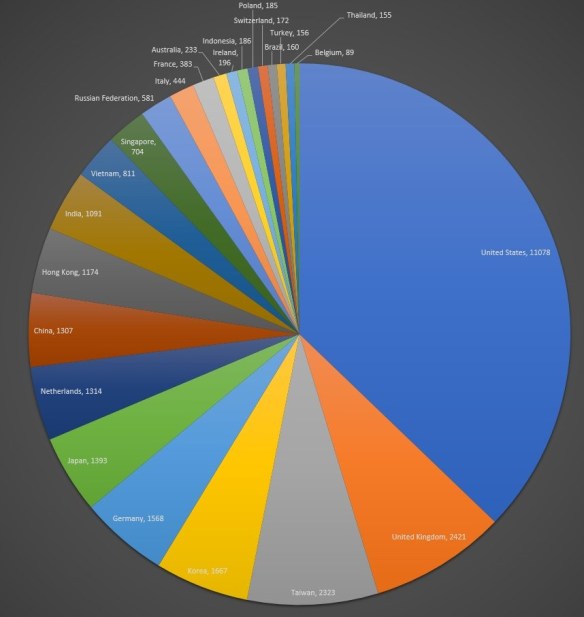
Tweeted by @belowzeroday, Cyberscoop, Apr 21
I shall try and put this in perspective, in the most entertaining manner I can. So, sit back, grab your morning Irish coffee and step inside my time machine.
Back in 2003 a computer worm made its way through the Internet. This worm infected thousands of systems, both commercial and personal. It ravaged and pillaged everything it could lay its crummy little paws on. It was finally detected in 2008, and given the name “Conficker”. I remember 2008 well. At the time, I was a system administrator for an IT consulting firm & was called upon many times to stomp this little critter. This worm was good, well coded, and went undetected for 5 years! It merged so well with Windows, it really didn’t affect the system’s performance. It was also very good at reproducing itself… kinda like George Forman.
Why was it so successful? How did it manage to get into so many systems? It was a flaw in Windows, much like the flaw leveraged by the exploits in the “ShadowBrokers” dump. Essentially… it’s 2008 all over again. Which begs the question, how long did the NSA have this exploit? Also, were they the only ones? If it took 5 years to catch “Conficker”, one can assume this flaw (and exploit) has been around for at least the same amount time (give or take a year).
So, I beg you, please don’t fear the Windows update window.
Let it run… Embrace it, enjoy it, whisper sweet nothings into its ear.
Because if you don’t, you only have yourself to blame if your browser history ends up on pastebin.
A message from you friendly neighbourhood hacker @loneferret
Ps. This flaw, and others, were fixed back in March of 2017. This piece was written in April 2017.






 In the realm of cyber criminals, The Lazarus Group are somewhat nebulous, hard to pin down, and known for their ability to die off and then resurrect themselves, hence their name. They’ve been identified as operating out of North Korea. To me, that means North Korea gives them a safe haven in return for services rendered. They are the bag man for their host supplying “dirty deeds”, just not done dirt cheap. Because nation states don’t do this stuff for themselves when they need to remain one step removed. Let me state that things are no where near this simplistic, and yes, China factors into this as well. But no surprise there given the long-standing partnership between China and North Korea.
In the realm of cyber criminals, The Lazarus Group are somewhat nebulous, hard to pin down, and known for their ability to die off and then resurrect themselves, hence their name. They’ve been identified as operating out of North Korea. To me, that means North Korea gives them a safe haven in return for services rendered. They are the bag man for their host supplying “dirty deeds”, just not done dirt cheap. Because nation states don’t do this stuff for themselves when they need to remain one step removed. Let me state that things are no where near this simplistic, and yes, China factors into this as well. But no surprise there given the long-standing partnership between China and North Korea.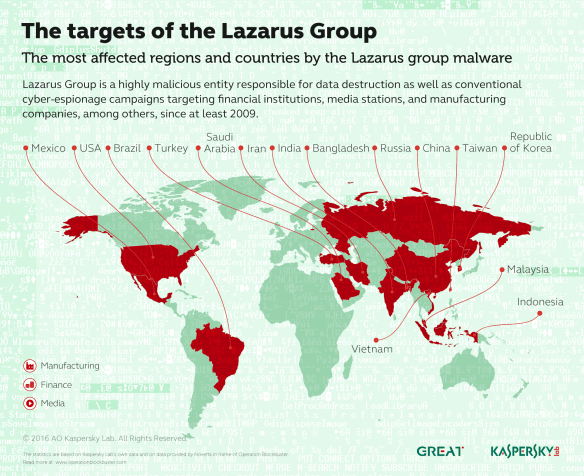 Where does this lead? Well, I did allude to the possibility of global economic chaos being used in the games nations play, because it’s all about the power and money is just a means to that end. Now we have news reports saying how nation states have resorted to robbing banks, and what a terrifying prospect that is. According to Richard Ledgett, Deputy Director of the NSA, in a story by the
Where does this lead? Well, I did allude to the possibility of global economic chaos being used in the games nations play, because it’s all about the power and money is just a means to that end. Now we have news reports saying how nation states have resorted to robbing banks, and what a terrifying prospect that is. According to Richard Ledgett, Deputy Director of the NSA, in a story by the