We all needed this page at one point. Or more. I know I did and thank you to the people in our community who had stuff like this for me to find. My turn to pay it forward 
“Do that thing which scares you”
I know. It seems so difficult. Feels so scary. But the best advice I can give you as you start out is this: give a talk. And CFP or Call for Presentations season is now in full swing, meaning deadlines and duedates need to be tracked. Deadlines can be 5 months before the Conference takes place. Don’t let this opportunity pass you by.
You may be able to start small, with a local meetup group. Someplace you feel comfortable, where you can talk for 20 minutes or more, on something you are excited to share and would love to explain.
Why talk? Why not just write or post? Well, a talk is more than just words on a screen. We get to see and hear your passion, which elevates your concept to another level. And we get to see – you! In a community of introverts, facetime is powerful. We love to learn by watching videos of talks given. Like yours. The other plus is that you get to attend a Con, which if you have read any of my posts, is both incentive and reward.
Where to even begin? Here. So relax and just start by reading to see what it is all about. There are people to reach out to in our community if you want to do this, like me. I am happy to be of help. @3ncr1pt3d on twitter :).
Watch the vidoes of past presenters from where you want to speak. Or those who talk about what you want to talk about. Know what has already been covered so you can bring something new. Or get a sense of what is trending. Plus, you can see how people deliver a talk. How slidedecks are put together. What humour works. An incredible resource is this site: http://www.irongeek.com . Adrian Crenshaw records talks at so many conferences. You’ll find whatever you need here.
Here are some terrific online resources to guide you:
https://thesweetkat.com/blog/. Kat Sweet has both given talks and evaluated them. Trust her. She is friendly, so smart, and very good at talks. Great starting place.
https://danielmiessler.com/blog/build-successful-infosec-career/#cfp. What you need to know about putting together a good talk. It starts with an idea that develops far beyond words on a page. You want to make sure you knkw about format, deadlines, requirements etc.
https://defcon.org/html/links/dc-speakerscorner.html#nikita-cfp. Now you are ready to hear the hard truth. Let’s make that paper stand out in a sea of submissions. You can be among the chosen, but only if you make your talk worthy.
https://www.helpnetsecurity.com/2016/03/30/how-to-get-your-talk-accepted-at-black-hat/ And then there is Black Hat. Why not aim high? Here are some suggestions to help you get noticed from one of the top-tier conferences, and Stefano Zanero, attendee and reviewer.
Is this your first time? Don’t be shy. We all had a first talk. And BSidesLV offers Proving Ground, a fantastic program at the start of their CFP phase to invite new speakers and pair them with a mentor. I know. That is how I started and it was amazing. Even better are the relationships you build here which carry forward, along with the learning. Because InfoSec is a community and our strength is in our people. Take a look here: https://bsideslv.org
Okay. Pep talk. You are good enough, smart enough and one of us. We want to hear what you have to say and we are willing to help you do it. Go for it!
You can find this under Learning

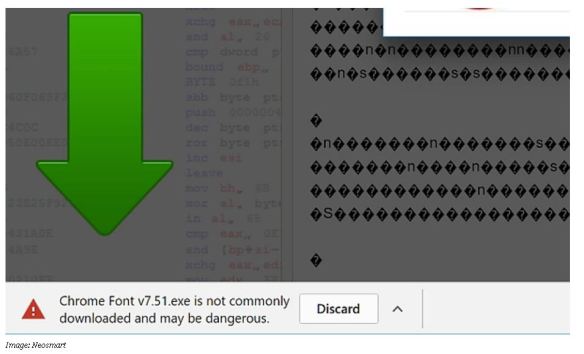 But, if you play it safe and do as Google says, click Discard and don’t download. You’ll avoid ransomware.
But, if you play it safe and do as Google says, click Discard and don’t download. You’ll avoid ransomware.