Yes, Virginia, you can hack a mainframe. My excellent friend, Phil Young, will be glad to show you how it’s done in his latest talk here from CA World 2016. “Gaps in Your Defense: Hacking the Mainframe”.
Category Archives: Uncategorized
Recommended Reading
 Red teams, Blue teams. Attackers vs Defenders. But what happens when you combine the best of both? Purple teaming!
Red teams, Blue teams. Attackers vs Defenders. But what happens when you combine the best of both? Purple teaming!
My very skilled friend, Haydn Johnson, has done a lot of research into this subject. As an adroit pentester himself, he knows about attack skills. And we’ve given a kickass talk on Blue Teams as well. Purple teaming is what happens when you take defending your realm to a whole new level. Give it a read and see what you think. “Top 4 Tips for Purple Team Exercises”
Parlez-vous le Hacking?

We have several really good infosec cons going on here in Canada. One of these is Hackfest, billed as the “largest hacking event in Canada”, and is held in la belle province, Quebec. which celebrated their 8th year. With the feel of DefCon, but at a much smaller scale, Hackfest invites the true spirit of exploration and hacking. Talks are diverse, concepts are challenging, and people are really friendly. But what Hackfest has become reknowned for is its CTF. I got to do my first CTF here this year, at a Saturday night party that was more fun than any I’ve been to in ages. Everyone was having a great time, playing together, enjoying the music and light show. Hats off to you, Hackfest!
Hackfest also features outstanding training courses – the kind that are really hard to get. I’m not there yet, but this year they had an intense Corelan course and yes, people were developing exploits within 2 days.
Then there were the talks. Where do I begin? Chris NIckerson brought it with his talk on Adversarial Simulation. The industry needs reform, and he outlined a ground-breaking, earth-shaking plan on how to get us where we need to be. To move beyond colours in a crayon box. It’s about selling integrity with the service, actually making security happen even when it’s hard. I talk about getting people out of their silos and collaborating – Chris and his compadres actually wrote the plan. Big things are in store, if we are willing to listen to some of the brightest and most experienced minds out there. 
My friend Stephanie Carruthers, #Sn0ww, enthralled (yes!) a roomful of attendees with how to do OSINT really well. She operates her own consulting business and advises clients on social engineering, vishing, phishing and some other dark arts.
@Renderman and pal, Murdoch Monkey, gave the talk everyone was talking about with “Hacking the Internet of Dongs.” Because really, was there a better time and place to do this? How much fun can you have on a Saturday afternoon 😉
And I had the pleasure of giving a talk on revamping Blue Teaming with my buddy Haydn Johnson. There’s nothing like a shot of whiskey before giving a 10:00 am talk. We built it from a webinar we had given for Dark Reading on how to do effective IT threat security analysis. We delved into some of our favourite things: data, monitoring, data, context; more data, the enhanced cyber kill chain and the OODA loop. It was a fantastic experience and deserves its own post. See the prezzie at http://www.slideshare.net/haydnjohnson/blue-team-reboot-hackfest
Then, at 11:00 I got to talk about some of my favourite things in A Stuxnet for Mainframes. Yes! 2 talks at Hackfest. Poutine, sight seeing – it all went by too quickly. But, there’s always next year. A bientot!
New and Improved!
Welcome to my bigger, better site! I really had to learn and earn my way up to this, and the goal is to make it worth your while to land here. Let this be a resource for you, an acknowledgement of the incredible talent within our community, a sharing of ideas and information to enrich our work and passion. So, in addition to my blog, because I just can’t seem to say enough about security, I have a daily updates section – my “catch of the day” offerings. As well, I have a page dedicated to resources, links to sites and people whose knowledge makes a difference, and my goto sources. And then, because I am all about threat intel and connecting dots, I have added an entire section under “Event”. Here you’ll find what I’ve been compiling on my favourite categories to track trends and look for patterns: ransomware, APTs, banking heists, ICS SCADA (whoa Stux!), DDoS, breaches and IoT Idiocy. Because when it comes to infosec & learning – I just can’t get enough.
October: Cyber Security Awareness Month
 October is Cyber Security Awareness Month. Bottom line is this: you own your own security. Much as you want to delegate it to the big guys or buy shiny blinky boxes that scan everything, you know your sh*t better than anyone else. Don’t pass the buck. Play an active role in your defense.
October is Cyber Security Awareness Month. Bottom line is this: you own your own security. Much as you want to delegate it to the big guys or buy shiny blinky boxes that scan everything, you know your sh*t better than anyone else. Don’t pass the buck. Play an active role in your defense.
TIP: Reduce, reuse, recycle does NOT apply to passwords. Make ’em long, keep ’em strong, and NEVER across multiple accounts.
An Unscheduled Hiatus

I know. It’s been a while. Life has a way of happening, and believe me, mine has been happening. I needed to take some personal time to just deal with everything and get my head above water. Drama is messy stuff.
There’s a lot to be gained when you can leverage learning from personal experience. And trust me, what I have to share in the months ahead will hopefully support others who’ve been through similar circumstances, and haven’t been able to regain their strength or their footing. I’m just really, really glad to be back in a place again from where I can write, as I can breathe.
It has been a year of extraordinary highs and lows. I have been so fortunate to realize opportunities I’d only dreamed of, experiences that I will treasure for life, and answers to prayers I had not said aloud. As a counterbalance I have lived through what I would not wish on another human being, and had to give up what had been my life in order to rescue myself and reclaim my life. Cryptic? Well, I am @3ncr1pt3d for a reason.
Through all of this I have been blessed by friends who stood by me, steadfast and true, unlike other people in whom we are told to put our trust. These friendships stand as pillars of truth to me, reminders that it is worth fighting for what we believe, even when we think we stand to lose all, or fear we may stand alone. Family and home should never mean having to apologize for or explain who you are, or god forbid, being afraid or ashamed to be your own person. You, my friends, know who you are, and that you have my eternal gratitude and love. And I will be there for you, and for others, as you have been here for me.
Finding my way to the Security community was like finally finding my way home. I have met some extraordinary people on my journey, and am learning so much from them. These relationships are gifts that enrich my life, just as everyday is a reward in itself of learning and personal growth. I know how lucky I am to find the thing I truly love, and do it. But like many others here, the price I paid cannot be measured in dollars.
So now, here I am, resolute, renewed, and ready for the next stage of this great adventure. I hope you’ll join me!
The Future of Ransomware

Ransomware is like like a nasty game of tag: you can try to avoid it but once you’re hit, you’re out. For all we know about doing defence right, following the best practices advocated by NIST and SANS, this particularly malevolent threat has been on an upward trajectory out of the gate since 2016, after trending through 2015. It’s gone way beyond just phishing for targets and locking down individual files. Current strains are evasive: like tag, they figure out what anti-virus and security is running on the target system that might detect it and stay hidden. They now go after websites. They lock down entire servers. And they don’t care who the victims are – not even hospitals.
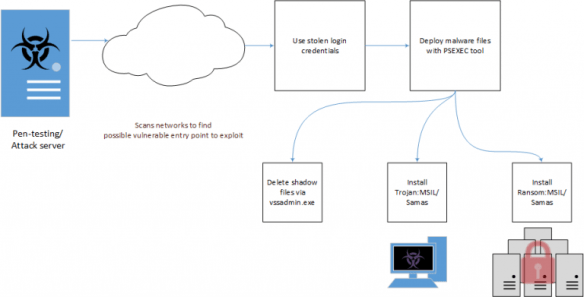
If you’ve been reading along with me on Twitter, or happen to be up at 2:00 a.m. like I am, you know that ransomware is what keeps me up at night. Along with some other brilliant minds in our security community who are dedicated to tracking and shutting down this ever-growing threat. These guys really know what they’re doing. Countless hours of research, investigation and analysis have produced this paper: Ransomware: Past, Present, and Future. There are definitive pieces that give the lay of the land and map out the course ahead. That is what this piece does. Sincere appreciation for the efforts of @da_667 @munin @ImmortanJo3 @wvualphasoldier (and others) who put this together. They understand just how widespread the risk is, and time is not a luxury we have. This is essential reading for anyone in tech, security, business, critical infrastructure. Essentially, anyone who needs to safeguard the data and networks their daily business relies on.
From the Talos blog: A fictional Adversary’s workflow of compromise and takeover

Right now, here is what I would advise anyone. Back you stuff up, frequently, and separately from the network. Check your patch management situation. Where are your exposures? How are you handling security awareness, especially around phishing? Do you monitor your systems regularly, so that you have a baseline to compare events against?
And finally, take the time now and please read this: Ransomware: Past, Present and Future by Talos. Because the more people who know about ransomware and where it’s headed, the better we can all work together to secure things.
Thank you for stopping by!
Apple vs the FBI: The Case for Privacy

This is about backdoors and Pandora’s boxes. It is monolithic in its implications, and everyone who is anyone right now is weighing in. Because this matters. Start by reading the letter by Tim Cook and Apple, defending privacy against dangerous precedents. My stance here does NOT justify the behaviour or actions of the terrorists in San Bernardino, or terrorism anywhere. This is about our privacy, and our rights. And once the decision is made, there will be no turning back.
February 16, 2016
A Message to Our Customers
The United States government has demanded that Apple take an unprecedented step which threatens the security of our customers. We oppose this order, which has implications far beyond the legal case at hand.
This moment calls for public discussion, and we want our customers and people around the country to understand what is at stake.
The Need for Encryption
Smartphones, led by iPhone, have become an essential part of our lives. People use them to store an incredible amount of personal information, from our private conversations to our photos, our music, our notes, our calendars and contacts, our financial information and health data, even where we have been and where we are going.
All that information needs to be protected from hackers and criminals who want to access it, steal it, and use it without our knowledge or permission. Customers expect Apple and other technology companies to do everything in our power to protect their personal information, and at Apple we are deeply committed to safeguarding their data.
Compromising the security of our personal information can ultimately put our personal safety at risk. That is why encryption has become so important to all of us.
For many years, we have used encryption to protect our customers’ personal data because we believe it’s the only way to keep their information safe. We have even put that data out of our own reach, because we believe the contents of your iPhone are none of our business.
The San Bernardino Case
We were shocked and outraged by the deadly act of terrorism in San Bernardino last December. We mourn the loss of life and want justice for all those whose lives were affected. The FBI asked us for help in the days following the attack, and we have worked hard to support the government’s efforts to solve this horrible crime. We have no sympathy for terrorists.
When the FBI has requested data that’s in our possession, we have provided it. Apple complies with valid subpoenas and search warrants, as we have in the San Bernardino case. We have also made Apple engineers available to advise the FBI, and we’ve offered our best ideas on a number of investigative options at their disposal.
We have great respect for the professionals at the FBI, and we believe their intentions are good. Up to this point, we have done everything that is both within our power and within the law to help them. But now the U.S. government has asked us for something we simply do not have, and something we consider too dangerous to create. They have asked us to build a backdoor to the iPhone.
Specifically, the FBI wants us to make a new version of the iPhone operating system, circumventing several important security features, and install it on an iPhone recovered during the investigation. In the wrong hands, this software — which does not exist today — would have the potential to unlock any iPhone in someone’s physical possession.
The FBI may use different words to describe this tool, but make no mistake: Building a version of iOS that bypasses security in this way would undeniably create a backdoor. And while the government may argue that its use would be limited to this case, there is no way to guarantee such control.
The Threat to Data Security
Some would argue that building a backdoor for just one iPhone is a simple, clean-cut solution. But it ignores both the basics of digital security and the significance of what the government is demanding in this case.
In today’s digital world, the “key” to an encrypted system is a piece of information that unlocks the data, and it is only as secure as the protections around it. Once the information is known, or a way to bypass the code is revealed, the encryption can be defeated by anyone with that knowledge.
The government suggests this tool could only be used once, on one phone. But that’s simply not true. Once created, the technique could be used over and over again, on any number of devices. In the physical world, it would be the equivalent of a master key, capable of opening hundreds of millions of locks — from restaurants and banks to stores and homes. No reasonable person would find that acceptable.
The government is asking Apple to hack our own users and undermine decades of security advancements that protect our customers — including tens of millions of American citizens — from sophisticated hackers and cybercriminals. The same engineers who built strong encryption into the iPhone to protect our users would, ironically, be ordered to weaken those protections and make our users less safe.
We can find no precedent for an American company being forced to expose its customers to a greater risk of attack. For years, cryptologists and national security experts have been warning against weakening encryption. Doing so would hurt only the well-meaning and law-abiding citizens who rely on companies like Apple to protect their data. Criminals and bad actors will still encrypt, using tools that are readily available to them.
A Dangerous Precedent
Rather than asking for legislative action through Congress, the FBI is proposing an unprecedented use of the All Writs Act of 1789 to justify an expansion of its authority.
The government would have us remove security features and add new capabilities to the operating system, allowing a passcode to be input electronically. This would make it easier to unlock an iPhone by “brute force,” trying thousands or millions of combinations with the speed of a modern computer.
The implications of the government’s demands are chilling. If the government can use the All Writs Act to make it easier to unlock your iPhone, it would have the power to reach into anyone’s device to capture their data. The government could extend this breach of privacy and demand that Apple build surveillance software to intercept your messages, access your health records or financial data, track your location, or even access your phone’s microphone or camera without your knowledge.
Opposing this order is not something we take lightly. We feel we must speak up in the face of what we see as an overreach by the U.S. government.
We are challenging the FBI’s demands with the deepest respect for American democracy and a love of our country. We believe it would be in the best interest of everyone to step back and consider the implications.
While we believe the FBI’s intentions are good, it would be wrong for the government to force us to build a backdoor into our products. And ultimately, we fear that this demand would undermine the very freedoms and liberty our government is meant to protect.
Tim Cook
My InfoSec Least Favourite Things
2015 has been one heck of a year for those of us in the Security Community. I’d like to pay a little hommage to the year that was, and celebrate the incredible community that is – InfoSec!
(to the tune of that famous ditty from Sound of Music)
Three heads of state who do not get encryption

Fighting the black hoodie hacker description (I wear purple)

Cleaning up after what Patch Tuesday brings
These are my InfoSec least favourite things
Munin’s got lore
Lesley helps more
DA’s Storytime
This is what’s great when you’re in InfoSec
Security hack sublime
EULA and Wassenaar setting the rules

Researchers disclose to be treated like fools
Zero day brokers who act like they’re kings

These are my InfoSec least favourite things
BSides reaches

Each con teaches
We’ve got stuff to share
This is what’s great when you’re in InfoSec
Security hackers care
Shadow; BYOD; Password disgrace

No DRP or insurance in place
Check mark security, blinky box pings
These are my InfoSec least favourite things
When we mentor
When we disclose
When we all unite

This is when InfoSec truly is great
Hack all the things – that’s right!
Big Data, Big Problems
In the wake of the recent VTech breach big questions are being raised about Big Data. It’s prompted an excellent response by many knowledgeable folks within infosec which is good, because this is a conversation we’ve needed to have for some time. The data just keeps building and I hate to say this but any sense of control we think we may have over it, especially as regards our Privacy, is illusory at best. Right now what I see is the Titanic sailing straight into a massive iceberg of insecurity.
I wrote a piece in response for LinkedIn Pulse, but I want to build off that here, because there is so much more that needs to be said. We’re battling a culture of entitlement and indifference, which casts a dark shadow across everything we think we know and understand. BYOD reigns supreme. The IOT has run amuck right into our once-regulated work spaces. And when it comes to IT, now it seems everyone is doing it for themselves. Because who needs guidelines when you’ve got google? It’s not just the stuff, it’s the attitude. Which is creating a huge problem: how do we secure what we don’t know?
So what’s going on with BYOD anyway? The view from the trenches isn’t pretty. ”cyber security policy success is having the authority to tell the userbase no and having that decision stick.” @da_667 tweet and “telling users no, when it matters, to protect themselves and your company network” @lslybot tweet #abusepolicy. How do we regulate a society that is essentially device-driven?
It isn’t just the servers and desktops at the office… everywhere we go, anything we touch – we’re connected. Fitbits, Applewatches, tablets, flash drives, Smartphones – this ability to portably “plug in,” and then help ourselves is one we don’t understand and we’ve lost any control over it we had.
In our corporate realm, we have regular users and superusers. And for good reason. We need privileges in order to do certain things and we need privilege hierarchies to establish the right levels of access. With higher levels of privilege come higher levels of risk. The problem is that what we’re seeing happen in organizations and companies is a less discriminating assignment of privilege.
We have all these devices, and a pervasive BYOD culture, demanding access to the networks and the data, all that lovely “big data”. And so we comply. We keep opening doors that should just. Stay. Closed.
When it comes to Access and Privileged identity management, we aren’t controlling what we can and need to control. Per Erika Chikowski, while 92 percent of organizations in the US have some user monitoring in place only 56 percent are handling privileged identity management. Almost a third of those companies do not have someone actually analyzing or auditing how and when employees and contractors have privileged access to systems on even a weekly basis. Meanwhile, 60% of IT decision makers admit to sharing their credentials.
In her recent piece “Employee Password Habits that Could Hurt Enterprises“, Erica shows that we’re still not learning despite recent breaches and training programs. As the line between personal and professional grows more blurry, 60% of employees do work activities from a personal device and 55% of employees do personal activities on work devices. Work data is accessed from personal devices more than once a day by over one third of employees. Passwords remain an Achilles heel that the most novice attacker can exploit to gain access to our networks and then find their way, or stumble upon, our corporate crown jewels. Half of employees reuse passwords at work and that number only increases for personal use. Remember that blurred line – it factors in here.
Cutbacks and reductions mean fewer guardians at the gate in IT. Under pressure to keep things running and meet demands, we resort to the path of least resistance so that we are “simplifying the process.”
Okay. Why not enable users to resolve some of their own problems by raising their status?
What the heck? Let Marketing have access to all the data – it’s just reports.
Why not? Let people update corporate social media accounts – there’s nothing to worry about there.
But here’s the bottom line: Privilege loses its meaning when that account status is being freely handed out.
“It is scary to think that this many people consider it normal for employees to have access to data that they shouldn’t have and for companies to not know where their missing data has gone.”
– David Gibson, VP at Varonis.
One word: exposure.
It is as bad as it sounds. When an employee shares company data from a mobile device with an unauthorized app or third party, he or she is a mere click away from placing corporate data at a significant risk. Data leaks can also be caused by application vulnerabilities exploited by malware. According to a March2015 IBM-Sponsored Ponemon institute Study, nearly 40 percent of companies, including many in the Fortune 500, aren’t properly securing the mobile apps they build for customers.
Add to that “9 in 10 websites leak user data to parties of which the user is likely unaware”. This is according to work done by Tim Libert of University of Pennsylvania. We are talking about siphoning and sharing data everywhere. So when Joe from work goes to a site like AirBnb to book his trip to Regina, the user data gets sent to 9 other sites on average . These include Google, Facebook and WordPress. Factor in that 6 in 10 sites generate third-party cookies, while 8 in 10 load javascript from external parties onto users’ computers. How do you control what you don’t even know?
This scenario is bad enough for your personal information. Now imagine an employee is accessing unauthorized sites. And don’t count on the Do Not Track me setting in the browser. Press it all you like. It’s like that button at the traffic light. Nothing really happens.

There are a whole host of security issues when it comes to data. So what happens when individuals operate as individuals, and make independent decisions about data storage and transmission? What do you do when your greatest security threat comes from within?
Lets talk Legalities. While business may love that employees pay for their own devices, and BYOD is all about convenience, it comes at a cost and everyone needs to be prepared. You can’t protect what you don’t know. And with Shadow it/Shadow data, you are exposed. I’ve spoken with Chris Case, the resident expert on cyber insurance at Dan Lawrie insurance brokers. Most businesses have no idea what they are really covered for. Here’s a sobering thought: the insurance you currently have won’t cover breaches. You need Errors and Omissions, and to make sure your riders address the new cyberrisks your data and reputation face. No. Insurance does not replace good security fundamentals, but it is a mandatory component in your security toolkit.
Let me reiterate something Mark Nunnikhoven recently wrote in his recent piece “The Attack Surface of Data” on LinkedInPulse. He re-establishes a point we all need to remember: The more data you have, the greater the value it is, then the greater your risk. But people keep putting more data out there, and storing it in places it can’t be kept safe. Mark points out that, as we here know too well, security is an after-thought at best. “Typically security teams are faced with dealing with the aftermath of collection decisions. That’s unfortunate because the easiest way to secure the data is simply not to every have it in the first place.”
The situation has evolved drastically from what we are used to protecting. This requires a different level of data breach prevention at the point of network entry. One where we need to really understand the risk profile of the device and the user.
“It’s not good enough to merely resist the rise of BYOD, if people can still access corporate e-mail when they get home…”
John McAfee
Because at the end of the day, what do our continued efforts to secure the corporate walls mean when this is the current reality?


