Find yourself mystified by all the acronyms and terms you hear when anything tech comes up? You don’t want to speak it – you just wish you knew what the heck it meant. No problem. In today’s Friday Fun installment, I’ll get you up to speed. Thanks to the fine folks at Raytheon, (sponsors of this excellent endeavour, the National Collegiate Cyber Defense Competition NCCDC) I can share this glossary of terms. And consider yourself just that much more up to speed on your own safety and security!
Find yourself mystified by all the acronyms and terms you hear when anything tech comes up? You don’t want to speak it – you just wish you knew what the heck it meant. No problem. In today’s Friday Fun installment, I’ll get you up to speed. Thanks to the fine folks at Raytheon, (sponsors of this excellent endeavour, the National Collegiate Cyber Defense Competition NCCDC) I can share this glossary of terms. And consider yourself just that much more up to speed on your own safety and security!
InfoSec Geek Speak Glossary
@ — Symbol chosen by Ray Tomlinson, a Raytheon BBN Technologies engineer who sent the first Internet email, to separate the names of users and their networks in addresses.
Advanced Persistent Threat — A group, such as a government or a criminal organization, with the expertise, resources and intent to target a specific entity. An APT uses multiple methods to break into a network, avoid detection and harvest valuable information over a long period of time.
Air gap — To physically separate or isolate a secure network from other unsecured systems or networks.
Back door — A hidden entry to a computer, network or software that bypasses security measures.
Blackhat — A criminal hacker who breaches security for malicious reasons or personal gain.
Blue Team — A group defending a computer system from mock attackers, usually as part of a controlled exercise. During the Raytheon National Collegiate Cyber Defense Competition the blue teams are made up of students.
Bot — A program that automates a simple action. Bots infect computers and secretly perform activities under the control of a remote administrator.
Botnet — A collection of computers infected by bots.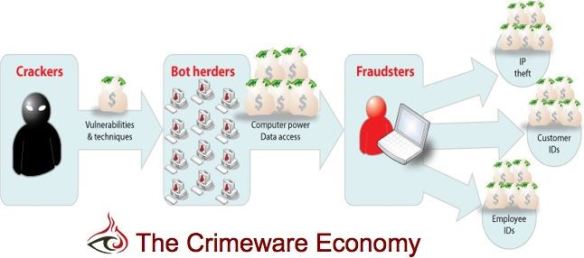
Bot master or herder —Someone who controls a botnet.
DoS Attack — A Denial-of-Service attack disrupts a website, server, or network resource – often by flooding it with more requests than it can handle.
DDoS Attack — A Distributed Denial of Service Attack is a DoS attack using a multitude of machines. Hackers often control one “master” machine to orchestrate the actions of “zombie” machines.
End-point Security — Security measures that protect a network from potential vulnerabilities posed by laptops and other mobile devices that access the network remotely.
Fuzzing — Automated input of invalid, unexpected or random data to a computer program. “Shocking” a computer in this way can reveal vulnerabilities.
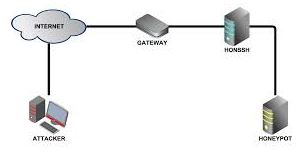
Honeypot — A trap set to detect intruders. A honeypot usually simulates a real network but is actually isolated and monitored so it can give advance warning of an intrusion.
Insider threat – A threat posed by employees, contractors, business associates or other people who have inside access to a computer system. Raytheon is the No. 1 insider threat solution provider, protecting hundreds of thousands of endpoints.
Malware —Software designed to hijack, damage, destroy or steal information from a device or system. Variations include spyware, adware, rootkits, viruses, keyloggers, and more.
Patching —The process of updating software.
Pentest — Short for penetration testing, or trying to hack into a system to identify weaknesses.
Phishing — Tricking someone into giving away personal information by imitating legitimate companies, organizations, or people online. The “ph” derives from phreaking, or “phone freaking” — hijacking telephone lines. Spearphishing focuses on a particular target.
Pwned — Pronounced like owned with a “p” at the beginning, pwned means to defeat security measures. Derives from the word “own,” or dominate.
Red Team — A group of cybersecurity professionals authorized to simulate an attack. A “blue team” of students will face a red team at the Raytheon National Collegiate Cyber Defense Competition.
Social Engineering —Manipulating people into sharing private information.
White Team — A group responsible for refereeing an engagement between a red team of mock attackers and a blue team of cyber defenders.
Whitelist — The opposite of a blacklist, a whitelist is a list of people, groups or software OK’d for system access.
Zombie — An infected device that is used to perform malicious tasks under remote control. Botnets of zombie computers are often used to spread e-mail spam and launch denial-of-service (DoS) attacks.
Thanks for reading and remember … “You Own Your Own Security!”